Technology
The Complete Guide To Blowfish Encryption Algorithm {Updated}

The complete guide to blowfish encryption algorithm in 2020.Everything you need to know about Blowfish Encryption Algorithm.
Modern embedded systems need data security more than ever before. Our PDA’s store personal e-mail and contacts lists, GPS receivers and, soon, cell phones keep logs of our movements, and our automobiles record our driving habits.
Over and above all of this, users demand products that can be reprogrammed during normal use, enabling them to eliminate bugs and add new features as firmware upgrades become available.
Although you may think of it as a beautiful fish in the aquarium, Blowfish is also an encryption method that is a very strong weapon against hackers and cybercriminals. It is used in a wide array of products, including some secure e-mail encryption tool, backup software, password management tools, and TiVo.
What Is The Blowfish Encryption Algorithm?
Table of Contents
Blowfish is an algorithm which was developed by Bruce Schneier in 1993 to replace DES. This symmetric cipher splits messages into blocks of 64 bits and encrypts them individually. And later it was named as Blowfish Encryption Algorithm.
Blowfish can be found in several software categories ranging from e-commerce platforms for securing payments to password management tools, where it is used to protect passwords. It is definitely one of the most flexible encryption methods available. It is known in the market for its tremendous speed and overall effectiveness as it has never been defeated in the market.
Structure Of The Blowfish Encryption Algorithm
A blowfish encryption algorithm is a symmetric block cipher as the same key is used for both encryption and decryption. The key has to be kept a secret except for the sender and the receiver. This image shows a high-level example of the process of symmetric encryption.
A block cipher is basically a computer routine that takes any amount of plain text and converts it into coded text, or cipher-text. It performs this routine in chunks of texts called blocks. And in order for the text to be decoded on the other side of the transmission, the function must also generate a key to unlock the cipher-text.

Blowfish has a 64-bit block size and a key length of anywhere between 32 bits to 448 bits. It is a 16-round Feistel cipher and uses large key-dependent S-boxes. It is similar in structure to CAST-128, which uses fixed S-boxes. Here is a visual representation of the algorithm-

Terminology Behind Blowfish Algorithm
In cryptographic circles, the plaintext is the message you’re trying to transmit. That message could be a medical test report, a firmware upgrade, or anything else that can be represented on a stream of bits.
The process of encryption converts the plain text message into cipher-text, and decryption converts the encrypted message into plain text. Generally speaking, encryption algorithms come in two flavours, symmetric and public key.
Symmetric algorithms such as Blowfish use the same key for encryption and decryption. Public key encryption algorithms use two keys, one for encryption and another for decryption.
There are times when you want data integrity, the assurance that the recipient received the same message you sent. Encryption algorithms can also provide authentication, the assurance that the message came from whom it says it came from.
Sometimes, the encryption algorithm is restricted, meaning that the algorithm is itself kept a secret. But then you can never know for sure just how weak a restricted algorithm really is because the developer doesn’t give anyone a chance to analyze it.
How Does Blowfish Algorithm Work?
Blowfish uses a unique form of key generation. The second part of the Blowfish routine is a key expansion that converts a single key of up to 448 bits into a table of subkeys i.e. 4168 bytes in size. The creation of subkeys further increases security, because a hacker would have to crack more than just the original key.
You can see a simplifies version of how this works in the next image-
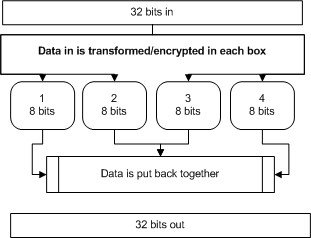
32 bits enter the algorithm. They’re split into four 8-bit boxes, transformed/encrypted, then put back together. Blowfish runs through this routine sixteen times. It is, therefore, an incredibly fast cipher that has a relatively simpler structure and is very effective.
Blowfish generates a really large key and this itself is a huge benefit to security. With the increase in the speed of computer processing, Blowfish is able to create a much longer key. And due to this it is much more difficult to try to hack the key value.
The Practical Example of Blowfish Algorithm
Let’s say an embedded system wants to establish a secure data exchange session with a laptop, perhaps over a wireless medium. At the start of the session, both the embedded system and the laptop compute a private Blowfish key and public and private RSA keys.
The embedded system and laptop exchange the public RSA keys and use them to encrypt and exchange their private Blowfish keys. The two machines then encrypt the remainder of their Blowfish communications using Blowfish. When the communications session is over, all the keys are discarded.
Blowfish Encryption Algorithm 101 – Conclusion
Now it is a good time to add start thinking about data integrity. And also adding privacy capabilities to your embedded system. The Blowfish algorithm is an excellent choice for encryption. This is a lightweight and is considered secure even after extensive analysis.
For more such posts, please check our technology section.

You must be logged in to post a comment Login